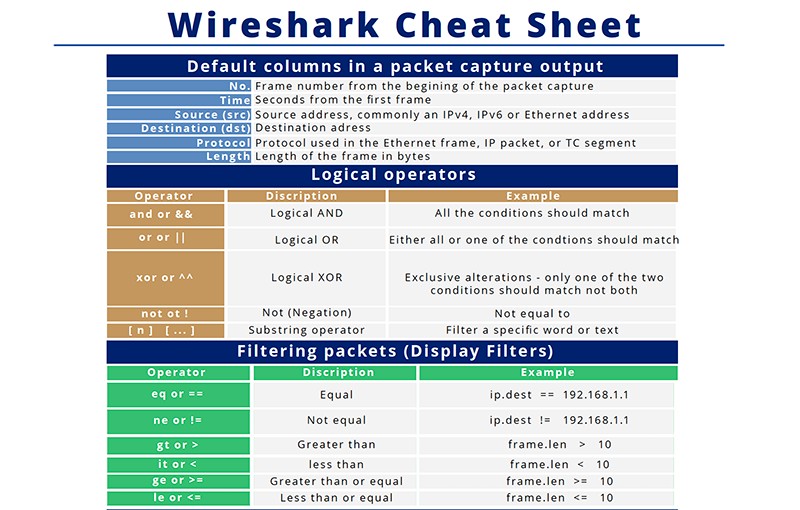
Wireshark Cheat Sheet
- Cracking & Hacking
- WIRESHARK, Wireshark Cheat Sheet, wireshark filters, wireshark guide, WIRESHARK TUTORIAL
- November 14, 2024
Wireshark, whose old name is Ethereal; It is a program that can run in many operating systems such as Windows, Linux, MacOS or Solaris and can analyze all the traffic going to network cards connected to computer. Analyze over 750 protocols Can capture packets and save them to a file.
Wireshark walkthrough the basics
Wireshark user guide
Setting up wireshark
How to Use Wireshark: A Complete Tutorial
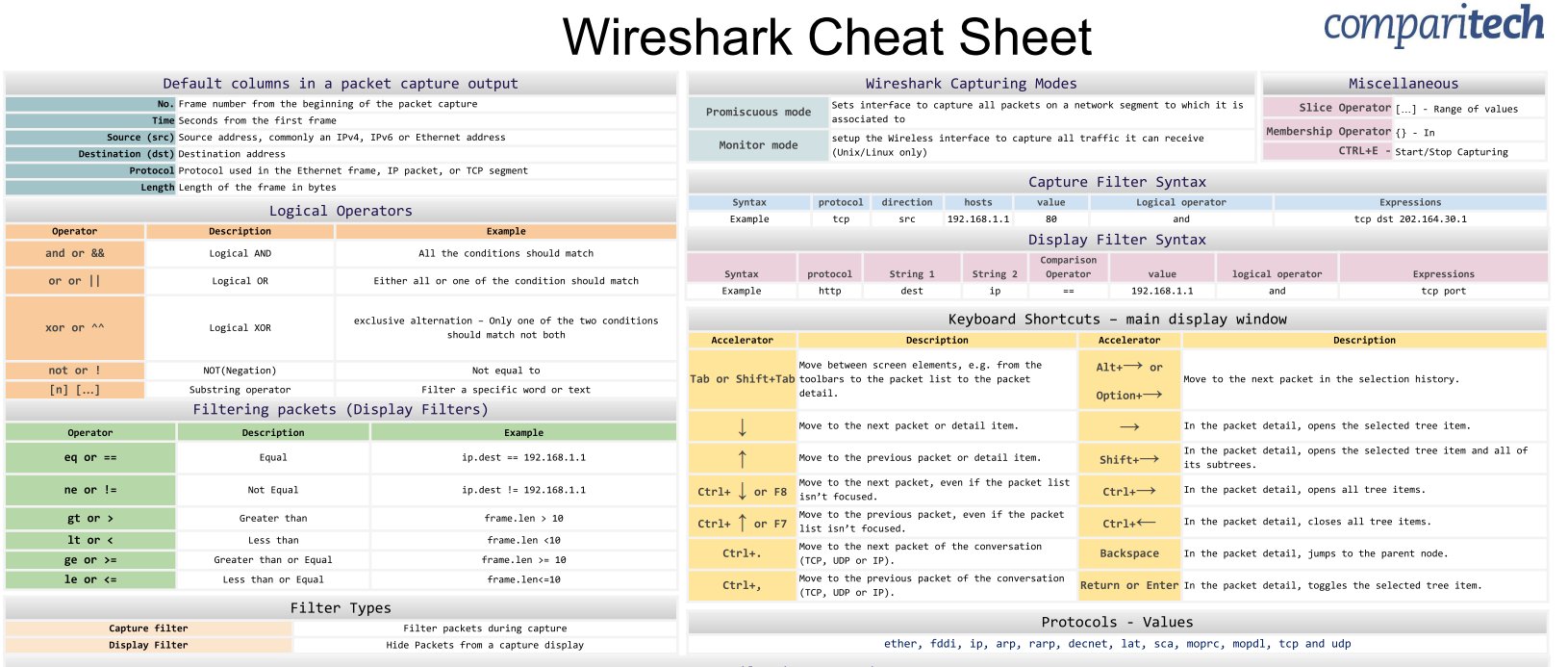
Wireshark Cheat Sheet
Logical operators are available for all filtering.
-
Example:
http & ip.src == 192.168.0.1 -
Management Frame: The frame for the connection between the network device and the client.
-
Control Frame: Controls the integrity of data traffic between the network device and the client.
-
Data Frame: The frame on which the original data is transferred.
Only to show the outgoing packets from the management frame.
wlan.fc.type==0
To show incoming, outgoing packets through control frame.
wlan.fc.type==1
To show packets transferred over the data frame.
wlan.fc.type==2
Association lists the requests.
wlan.fc.type_subtype==0
Association lists the answers.
wlan.fc.type_subtype==1
Probe lists requests.
wlan.fc.type_subtype==4
Lists the probe responses.
wlan.fc.type_subtype==5
Lists Beacon signals / waves.
wlan.fc.type_subtype==8
Lists the Authentication requests.
wlan.fc.type_subtype==11
Lists deauthentication requests.
wlan.fc.type_subtype==12
TCP lists the outgoing packets to the xx port.
tcp.port == xx
TCP lists packages with the Source xx port.
tcp.srcport == xx
TCP lists packages with a destination xx port.
tcp.dstport == xx
UDP lists the outgoing packets to the xx port.
udp.port == xx
UDP lists packets with a destination xx port.
udp.srcport == xx
UDP lists packages that have the Source xx port.
udp.dstport == xx
Lists the HTTP Get requests.
http.request
Lists packages for the source or destination mac address.
wlan.addr == MAC-Address
The source lists packages that have a mac address.
wlan.sa == MAC-Address
Lists packages that have a target mac address.
wlan.da == MAC-Address

Wireshark Filters
Filtering traffic from one server:
ip.addr eq <IP>
Filtering traffic between two servers:
ip.addr eq <IP1> and ip.addr eq <IP2>
Filtering traffic of standard protocols:
smtp
ldap
ssl
http
dns
Filtering an SMTP conversation between two servers:
ip.addr eq <IP1> and ip.addr eq <IP2> and smtp
Filtering an HTTP conversation between two servers:
ip.addr eq <IP1> and ip.addr eq <IP2> and http
Filtering an SMTP Conversation with TLS between two servers:
ip.addr eq <IP1> and ip.addr eq <IP2> and ssl
Filtering outgoing packets from ona particular IP:
ip.src eq <IP>
Filtering incoming packets from one particular IP:
ip.dst eq <IP>
Filtering the number of SMTP sessions:
smtp.req.command eq QUIT
Filtering the number of transmited mails:
Wireshark Filters:
smtp.req.command eq MAIL
Filtering the number of recipients in an SMTP conversation:
smtp.req.command eq RCPT
Filtering a specific recipient mailbox:
smtp.req.command eq RCPT and smtp.req.parameter contains “user@domain.com”
Filtering a specific sender mailbox:
smtp.req.command eq MAIL and smtp.req.parameter conatains “user@domain.com”
Filtering SMTP errors:
If you know the error code then use this filter:
smtp.response.code eq <ERROR_CODE>
for example: smtp.response.code eq 421
If you don’t know it, or if you want to list all SMTP errors in the SMTP sessions, then you must first exclude all the valid codes (2XX) until you end up only with 4XX or 5XX codes.
not smtp.response.code eq 220 and not smtp.response.code eq 221 and not smtp.response.code eq 250 and not smtp.response.code eq 354 and smtp.response.code
When you execute this filter you will end up only with 4XX and/or 5XX error codes so you will see all SMTP errors withing your capture. If it ends up blank, it means that no SMTP errors were found in that specific capture.
===========================================================================================================================
#Wireshark #PacketSniffing #NetworkSecurity #CyberTools #PenTesting
Leave Your Comment Here
You must be logged in to post a comment.




