
How to Create an Evil Twin Attack to Capture Wi-Fi Credentials
How to Create an Evil Twin Attack to Capture Wi-Fi Credentials Let’s say, You are an Ethical hacker and you are learning and trying to figure out how to gain access to a target network using various penetration testing techniques for education purposes. Before we Delve into ” How to Create an Evil Twin Attack to Capture WI-FI Credentials, first …
Read More

TL;DR (Quick Commands)
TL;DR (Quick Commands) Is your Kali running slow and need of a clean & boost? Well have no fear TLDR quick commands are here! sudo journalctl –vacuum-size=100M The cODe: sudo journalctl –vacuum-size=100M sudo rm -rf /var/cache/apt/archives/*.deb sudo systemctl disable –now bluetooth.service cups.service echo ‘vm.swappiness=10’ | sudo tee -a /etc/sysctl.conf && sudo sysctl -p sudo sync && sudo sysctl -w vm.drop_caches=3 …
Read More

How to hack a Website
How to Hack a Website Inspect the Page Source: Right-click on the page and select “View Page Source” or press Ctrl+U. Look for any comments or hidden elements that might contain hints or credentials. Click on the browser’s menu icon (often represented by three dots or lines) in the top-right corner. Hover over “More tools” and select “Developer tools” or …
Read More

Burp Suite Cheat Sheet
Burp Suite Cheat Sheet 🥴 Intro : Burp Suite is the de-facto penetration testing tool for assessing web applications. It enables penetration testers to test applications using features like repeater, intruder, sequencer, and extender. Burp Suite comes in a free community edition and a commercial professional edition. It has a built in Chromium browser for easy set-up of HTTP and SSL/TLS interception …
Read More
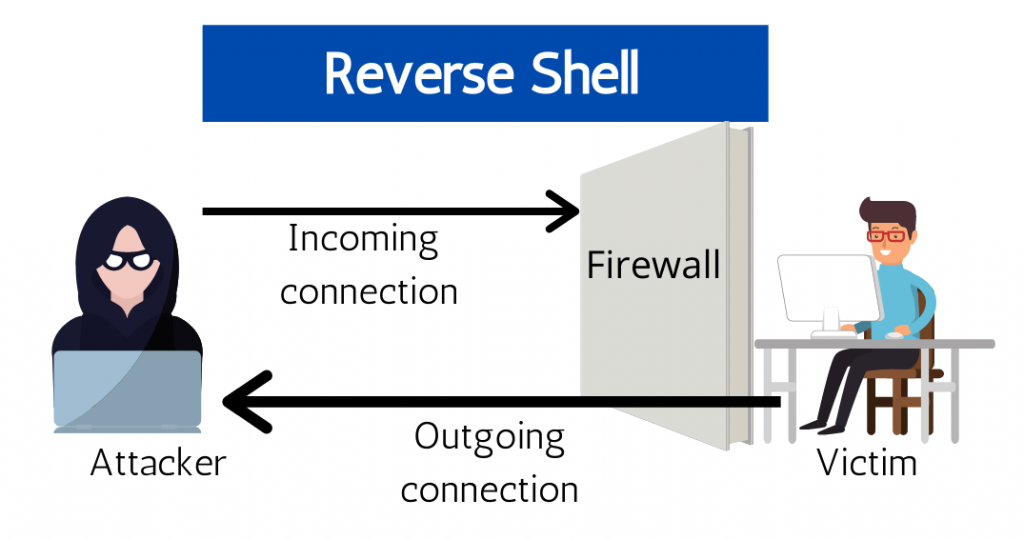
Reverse Shell Cheat Sheet
Reverse Shell Cheat Sheet PAYLOAD ALL THE THINGS Summary Tools Reverse Shell Awk Automatic Reverse Shell Generator Bash TCP Bash UDP C Dart Golang Groovy Alternative 1 Groovy Java Alternative 1 Java Alternative 2 Java Lua Ncat Netcat OpenBsd Netcat BusyBox Netcat Traditional NodeJS OGNL OpenSSL Perl PHP Powershell Python Ruby Rust Socat Telnet War Meterpreter Shell Windows Staged reverse …
Read More
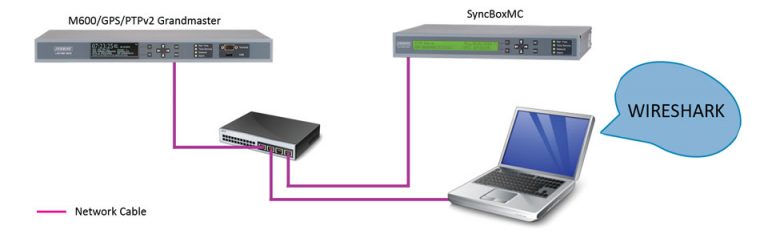
How to Setup Wireshark
- Cracking & Hacking
-
Aircrack-ng setup, How to Setup Wireshark, how to sniff wireless traffic, how to turn on a wifi adapter, network monitoring tool, network packet analysis, packet capture configuration, protocol analyzer setup, wireshark beginner tutorial, Wireshark installation
- November 14, 2024
How to Setup Wireshark To set up your laptop to capture and analyze wireless network traffic using Aircrack-ng’s airmon-ng and Wireshark, follow these steps: First Buy and Get the necessary equipment To capture and analyze wireless network traffic using tools like Aircrack-ng’s airmon-ng and Wireshark, it’s essential to have a compatible wireless network adapter that supports monitor mode and packet …
Read More
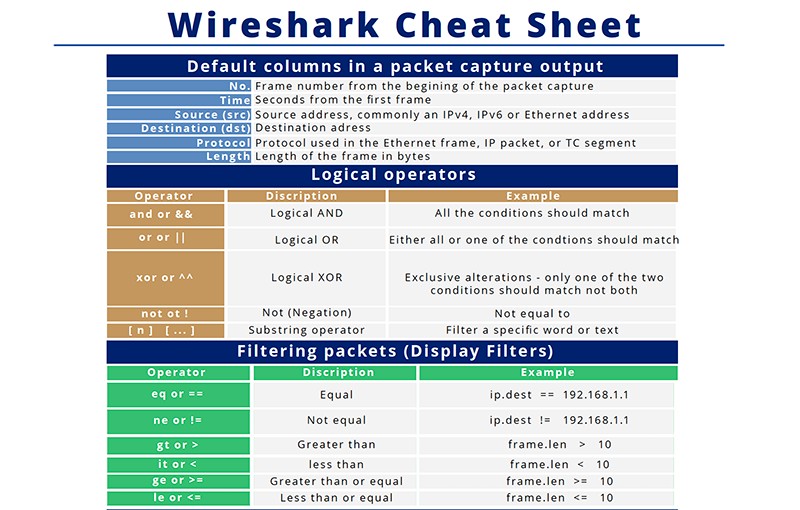
Wireshark Cheat Sheet
Wireshark Cheat Sheet Wireshark, whose old name is Ethereal; It is a program that can run in many operating systems such as Windows, Linux, MacOS or Solaris and can analyze all the traffic going to network cards connected to computer. Analyze over 750 protocols Can capture packets and save them to a file. Wireshark walkthrough the basics Wireshark user guide …
Read More
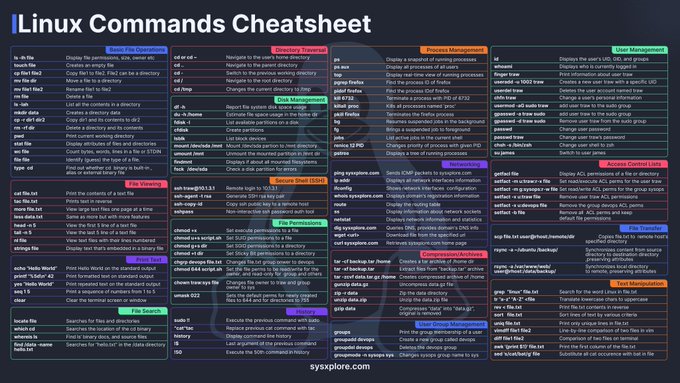
Linux Cheat Sheet
Linux Cheat Sheet Linux commands cheat sheet How to update/upgrade Linux: What does APT do? APT (Advanced Packaging Tool) is a set of core tools found inside the Debian operating system. It provides utilities for the installation and removal of software packages and dependencies on a system. apt is a subset of apt-get and apt-cache commands providing necessary commands for …
Read More
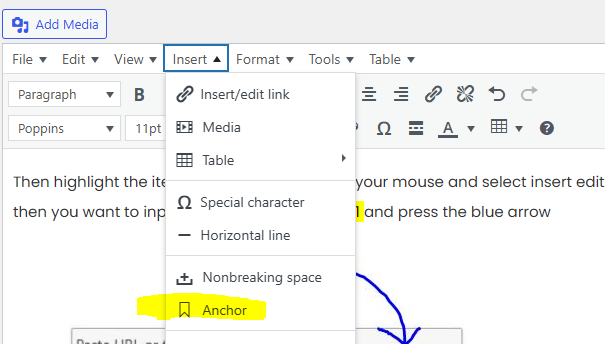
How to add Anchor Links in WordPress
How to add Anchor Links in WordPress How to add Anchor Links in WordPress, Learn how to create very easy anchor ids and links in WordPress. If you dont like using Gutenberg in WordPress like me, then you will find many of the tutorials on how to install anchor text not very good. So I put together this easy to …
Read More

Covering a broad Spectrum of Pentesting
Table of Contents Initial Scanning Port/Service Enumeration Port 21 — FTP Port 22 — SSH Port 25/110/143 — SMTP/POP3/IMAP Port 53 — DNS Port 80/443 — HTTP/S Port 139/445 — SMB/SAMBA Port 389/636 — LDAP/S Port 3306 — MySQL Port 3389 — RDP Shells File Transfers Privilege Escalation Initial Scanning The initial scanning phase is probably the most crucial aspect …
Read More









