
Lets hack your home network
- Cracking & Hacking
-
Android ADB exploit, brute force hacking, cybersecurity, ethical hacking, ethical hacking tutorial, find devices on network, hacking tools, home network security, MITM attack, network discovery, nmap scanning, open ports, penetration testing, router security, Windows SMB exploit
- February 12, 2025
Lets hack your home network Step 1: Network Discovery (Finding Devices) 1. Identify Your Network Subnet First, find your network’s IP range. Open a terminal and run: bash CopyEdit ip a | grep inet or bash CopyEdit ifconfig Look for something like 192.168.1.x or 10.0.0.x. The subnet is likely 192.168.1.0/24. 2. Scan the Network for Devices Use nmap to find …
Read More
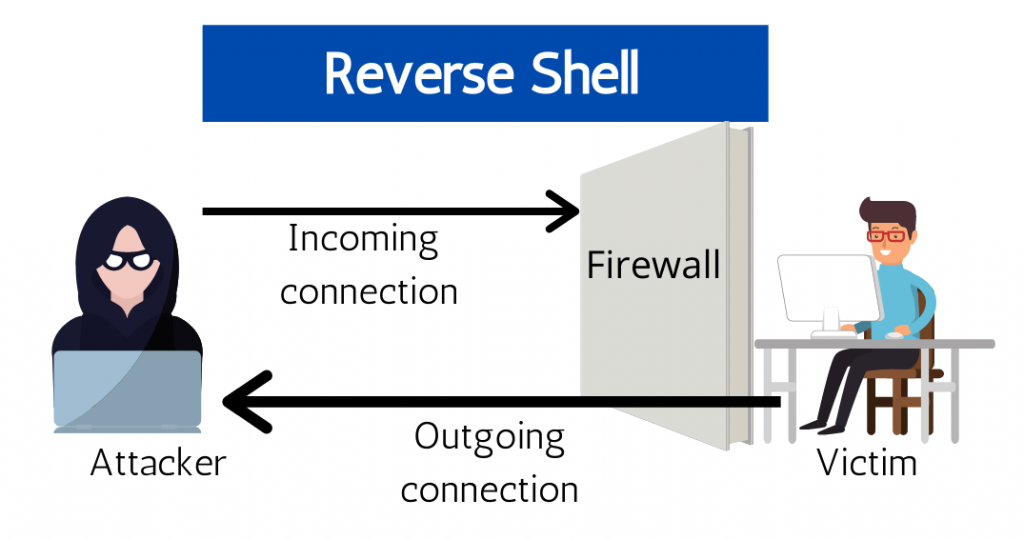
Reverse Shell Cheat Sheet
Reverse Shell Cheat Sheet PAYLOAD ALL THE THINGS Summary Tools Reverse Shell Awk Automatic Reverse Shell Generator Bash TCP Bash UDP C Dart Golang Groovy Alternative 1 Groovy Java Alternative 1 Java Alternative 2 Java Lua Ncat Netcat OpenBsd Netcat BusyBox Netcat Traditional NodeJS OGNL OpenSSL Perl PHP Powershell Python Ruby Rust Socat Telnet War Meterpreter Shell Windows Staged reverse …
Read More

Covering a broad Spectrum of Pentesting
Table of Contents Initial Scanning Port/Service Enumeration Port 21 — FTP Port 22 — SSH Port 25/110/143 — SMTP/POP3/IMAP Port 53 — DNS Port 80/443 — HTTP/S Port 139/445 — SMB/SAMBA Port 389/636 — LDAP/S Port 3306 — MySQL Port 3389 — RDP Shells File Transfers Privilege Escalation Initial Scanning The initial scanning phase is probably the most crucial aspect …
Read More
How to use theHarvester
How to use theHarvester What is theHarvester? theHarvester is an open-source intelligence (OSINT) tool designed to collect information such as email addresses, subdomains, IP addresses, and URLs from various public sources. It’s commonly used in the reconnaissance phase of penetration testing to map an organization’s external footprint. Why use theHarvester? Utilizing theHarvester enables security professionals to efficiently gather critical data …
Read More

Kali Linux Basics: Cheat Sheet for Beginners
- Cracking & Hacking
-
cc cleaner, clear logs, clear tracks after hacking, cracking & Hacking, kali linux, kali linux cheat sheet, log cleaner, penetration testing, remove logs, shred clearing tracks, timestomp
- November 13, 2024
💻Kali Linux Basics: Cheat Sheet for Beginners November 05, 2024 Table of Contents 🧭 Navigation & Directory Management 📝 File Operations 🔍 Search for Files and Text 📦 Package Management with APT 🔒 Permissions and Ownership 📊 System Monitoring 🌐 Network Essentials 💾 File Compression and Archiving 🔧 Process Management ⏰ Scheduling with Cron 🔑 SSH & Remote Access 🧭 Navigation …
Read More

Top 20 Bug Bounty Platforms to Earn Money from
- Cyber Security
-
bug bounty, bug bounty platforms, bug bounty programs, cybersecurity, cybersecurity awareness, cybersecurity community, cybersecurity professionals, cybersecurity rewards, digital security, ethical hacking, hacker community, online security, penetration testing, responsible disclosure, responsible disclosure policy, security research, security researchers, security testing, security vulnerabilities, web security
- December 14, 2023
Top 20 Bug Bounty Platforms to Earn Money from Earn Big Money Hacking Fortune 500 companies! At the heart of ethical hacking and responsible disclosure, bug bounty programs connect security-minded individuals with organizations seeking to identify vulnerabilities in their systems. This mutually beneficial arrangement allows you to leverage your skills, uncover security flaws, and earn money in the process. With …
Read More





