
How to Setup and Use Recon-ng
How to Setup and Use Recon-ng Setting up Recon-ng to install recon-ng you must have Python 3.6 or higher installed on your system, Please follow the instructions below to assist you in how to setup and use Recon-ng on your operating system. What is Recon-ng What is Recon-ng? Recon-ng is a web reconnaissance tool that automates information gathering to aid …
Read More

How to use BeEF
How to use BeEF BeEF (Browser Exploitation Framework) is a powerful penetration testing tool that focuses on exploiting web browsers. It is particularly useful for assessing the security of browser-based environments and understanding the risks posed by browser vulnerabilities. Here is a quick overview to help students understand how to use BeEF: What is BeEF? Purpose: BeEF is designed to …
Read More

How to Anonymously File Share
How to Anonymously File Share 📁 Anonymous File Sharing | How to Use Magic-Wormhole for Fast & Secure Transfers November 13, 2024 Looking for a way to send files quickly and anonymously without sharing your IP or username? Magic-Wormhole lets you securely transfer files between devices using a unique, one-time code. Here’s how you can get started! 🛠 Steps to Share Files Anonymously with Magic-Wormhole: Step 1: …
Read More

Kali Linux Basics: Cheat Sheet for Beginners
- Cracking & Hacking
-
cc cleaner, clear logs, clear tracks after hacking, cracking & Hacking, kali linux, kali linux cheat sheet, log cleaner, penetration testing, remove logs, shred clearing tracks, timestomp
- November 13, 2024
💻Kali Linux Basics: Cheat Sheet for Beginners November 05, 2024 Table of Contents 🧭 Navigation & Directory Management 📝 File Operations 🔍 Search for Files and Text 📦 Package Management with APT 🔒 Permissions and Ownership 📊 System Monitoring 🌐 Network Essentials 💾 File Compression and Archiving 🔧 Process Management ⏰ Scheduling with Cron 🔑 SSH & Remote Access 🧭 Navigation …
Read More

Can You Get Shodan Premium Membership for Free?
- Cracking & Hacking
-
Academic Affiliation, Academic Email, Academic Email Verification, Academic Resources, Can You Get Shodan Premium Membership for Free, cybersecurity, Cybersecurity Education, Cybersecurity Tools, Free Shodan Premium, IP Monitoring, Shodan Academic Membership, Shodan Academic Upgrade, Shodan Access, Shodan Features, Shodan Premium, Shodan Premium Benefits, Shodan Tutorial, Troubleshooting Shodan Upgrade., Vulnerability Scanning
- December 14, 2023
Can You Get Shodan Premium Membership for Free? In the dynamic world of cybersecurity, Shodan Premium is a valuable resource for professionals and enthusiasts alike. But what if we told you that there’s a way to access Shodan Premium for free? In this guide, we’ll explore the possibility of obtaining Shodan Premium without opening your wallet. With an academic email …
Read More

The Top 20 OSINT Resources of the Year
Elevate Your Open Source Intelligence Gathering Because resources are needed in the Cyber Security Field we put together this comprehensive list of The Top 20 OSINT Resources of the Year Discover the Best OSINT Tools and Websites It’s crucial to mention, In the ever-evolving landscape of cybersecurity and digital investigations, staying informed and well-equipped is paramount. To sum it up, …
Read More

Who is the group called the hand?
- Cracking & Hacking
-
Honeypot traps., Illegal activities online, ISP monitoring, Online anonymity protection, ProtonVPN, Surveillance and privacy, The Five Eyes intelligence alliance, The Hand secret society, Underground organizations, VPN security
- September 26, 2022
Who is the group called the hand? “The Hand and the Five Eyes: An Overview of an Underground Secret Society” “Explore the enigmatic world of ‘The Hand,’ an underground secret society, often portrayed in movies and TV shows. Discover their connection to ‘The Five Eyes’ intelligence alliance and the importance of safeguarding your online anonymity. Learn which VPNs to trust …
Read More
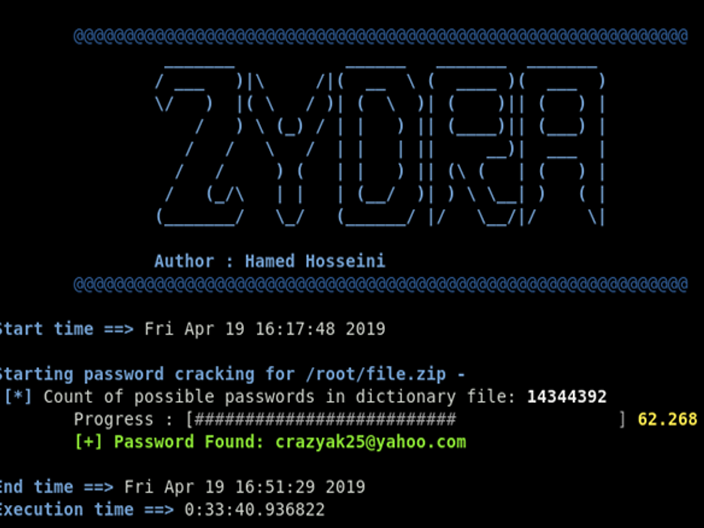
The Power of Zydra Cracking PDFS
- Cracking & Hacking
-
breaking PDF encryption, crack pdf, crack rar file, cracking encrypted PDF, decrypt PDF, hacking PDF files, password-protected PDF, PDF cracking software, PDF cracking techniques, PDF cracking tutorial, PDF decryption tool, PDF encryption, PDF hacking, PDF password attack, PDF password recovery, PDF security, remove PDF password, unlock PDF, winrar crack software, zydra, Zydra cracking tool, Zydra PDF crack, Zydra PDF cracking, Zydra PDF cracking guide.
- September 25, 2022
The Power of Zydra & Cracking PDFS “Unlock the potential of Zydra for PDF cracking. Explore the power of cracking encrypted PDFs effortlessly.” Some say, Eventually we find everything we are looking for on the internet, however, we never seem to be able to find the things we need at the time we need them. Zydra is no exception, It …
Read More







