
How to Secure Your Website
- Cyber Security
-
Cloudflare setup, CSRF protection, cybersecurity checklist, free website security, html site protection, HTTPS, malware removal, secure configuration, secure hosting, shopify security, SQL injection fix, SSL, WAF, web hardening, website protection, website security, wordpress security, XSS prevention
- October 23, 2025
How to Secure Your Website Three Methods: WordPress – Shopify – Self-hosted HTML site ( Top 25 list ) Securing your website doesn’t have to cost a dime — it just requires the right steps and consistency. Whether you’re running a WordPress blog, a Shopify storefront, or a self-hosted HTML site, there are free, proven methods to defend against hackers, …
Read More
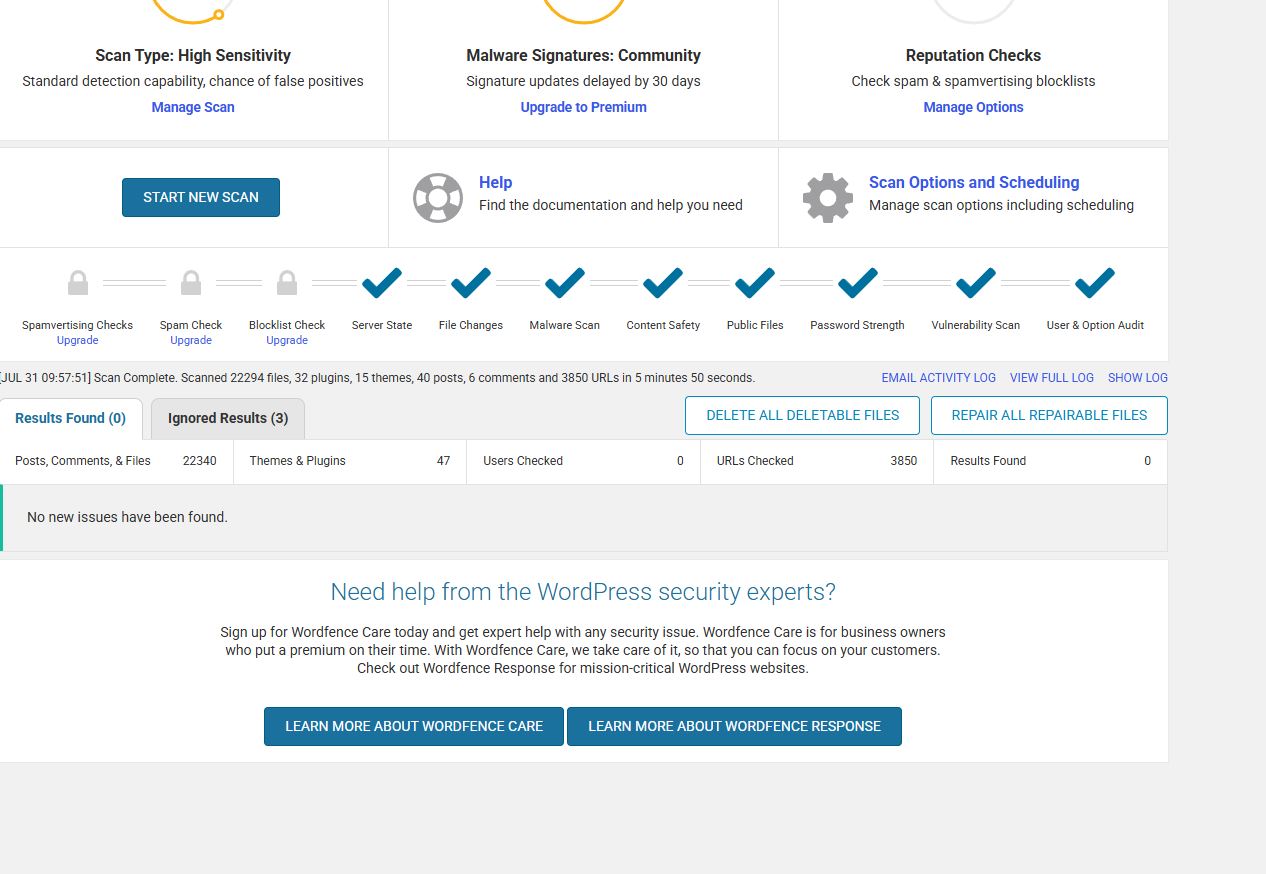
How I Secured My WordPress Blog – A Real-World Cybersecurity Walkthrough
- Cyber Security
-
blog hardening, cybersecurity, ethical hacking, free security tools, kali linux, secure blog setup, website security, website vulnerability, Wordfence, WordPress
- July 31, 2025
How I Secured My WordPress Blog – A Real-World Cybersecurity Walkthrough This post documents how I secured my WordPress blog using free tools, plugins, and configuration changes. The process simulates real-world website hardening and vulnerability management, which is useful for anyone studying cybersecurity, running a blog, or wanting to understand how attackers target insecure setups. Step 1: Scan Your Site …
Read More
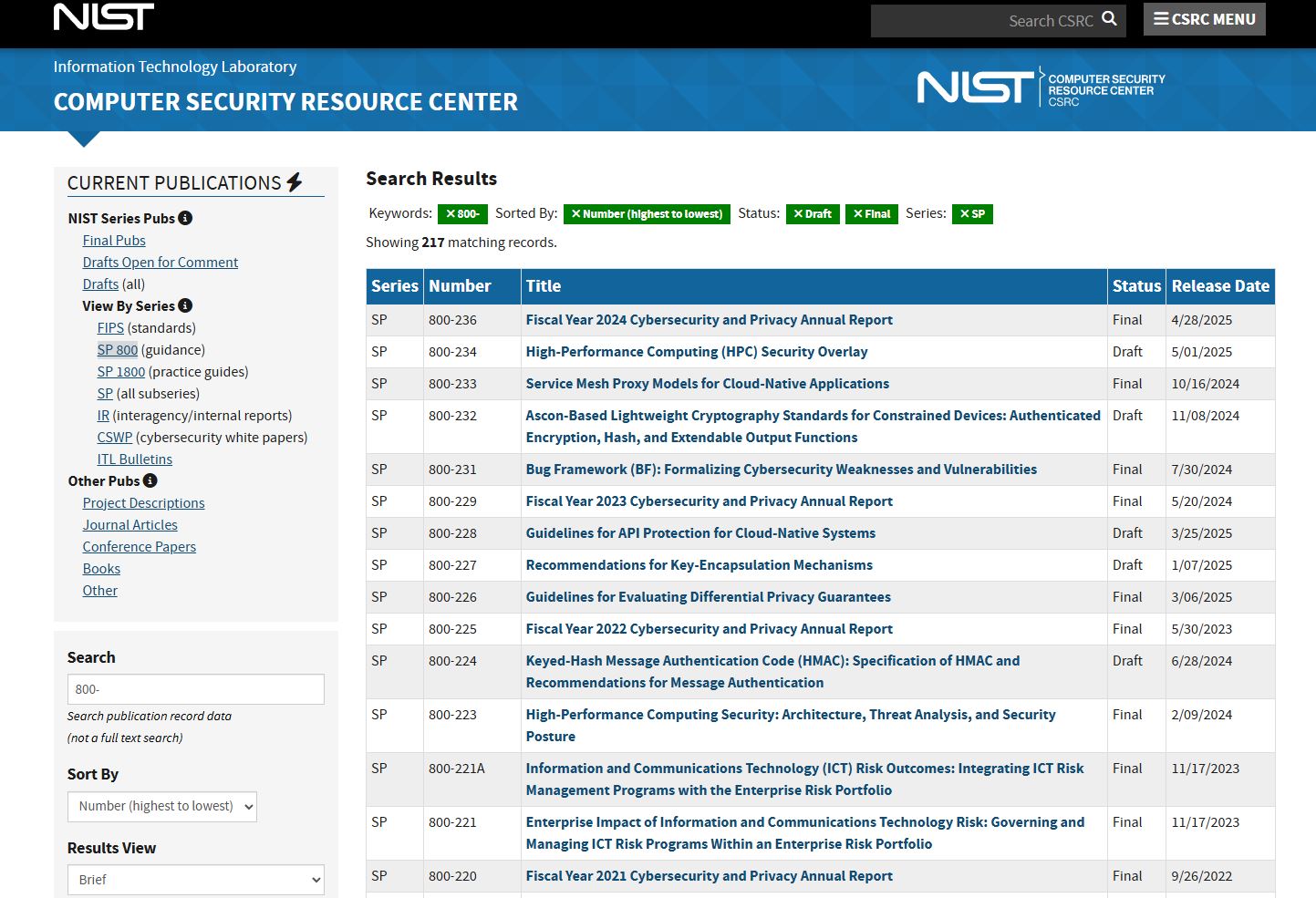
Download These Free NIST Cybersecurity Docs to Boost Your CISSP Prep
- Cyber Security
-
CISSP, cybersecurity, cybersecurity framework, federal security standards, Free NIST Cybersecurity Docs, free NIST PDF, How to download NIST guidelines, incident response, NIST, NIST list, NIST PDF Download, NIST research, NIST SP 800-53, risk management, security certification, SP 800 series
- May 31, 2025
Download These Free NIST Cybersecurity Docs to Boost Your CISSP Prep If you’re studying for the CISSP or working in cybersecurity, you need to know about NIST. The National Institute of Standards and Technology publishes free, authoritative guidelines that shape the backbone of modern cybersecurity. These documents—like SP 800-53 and the Cybersecurity Framework (CSF)—are not just useful; they’re foundational. In …
Read More

TL;DR (Quick Commands)
TL;DR (Quick Commands) Is your Kali running slow and need of a clean & boost? Well have no fear TLDR quick commands are here! sudo journalctl –vacuum-size=100M The cODe: sudo journalctl –vacuum-size=100M sudo rm -rf /var/cache/apt/archives/*.deb sudo systemctl disable –now bluetooth.service cups.service echo ‘vm.swappiness=10’ | sudo tee -a /etc/sysctl.conf && sudo sysctl -p sudo sync && sudo sysctl -w vm.drop_caches=3 …
Read More

Covering a broad Spectrum of Pentesting
Table of Contents Initial Scanning Port/Service Enumeration Port 21 — FTP Port 22 — SSH Port 25/110/143 — SMTP/POP3/IMAP Port 53 — DNS Port 80/443 — HTTP/S Port 139/445 — SMB/SAMBA Port 389/636 — LDAP/S Port 3306 — MySQL Port 3389 — RDP Shells File Transfers Privilege Escalation Initial Scanning The initial scanning phase is probably the most crucial aspect …
Read More

Cyber Security Tools
⋆.🌼 Cyber Security Tools❣ 🌼.⋆ Open Data Playground Shodan Images Link Expander – Grabify IP Logger & URL Shortener cyberguideme/Tools: Cyber Security Tools payloadbox/sql-injection-payload-list: 🎯 SQL Injection Payload List Z4KKD/CIS261ProjectPhase3 CTFd/CTFd: CTFs as you need them ctf-writeups/banana-boy.md at master · VulnHub/ctf-writeups sbilly/awesome-security: A collection of awesome security resources hmaverickadams/TCM-Security-Sample-Pentest-Report: Sample pentest report provided by TCM Security DvorakDwarf/Infinite-Storage-Glitch: ISG lets you …
Read More

Top 20 Bug Bounty Platforms to Earn Money from
- Cyber Security
-
bug bounty, bug bounty platforms, bug bounty programs, cybersecurity, cybersecurity awareness, cybersecurity community, cybersecurity professionals, cybersecurity rewards, digital security, ethical hacking, hacker community, online security, penetration testing, responsible disclosure, responsible disclosure policy, security research, security researchers, security testing, security vulnerabilities, web security
- December 14, 2023
Top 20 Bug Bounty Platforms to Earn Money from Earn Big Money Hacking Fortune 500 companies! At the heart of ethical hacking and responsible disclosure, bug bounty programs connect security-minded individuals with organizations seeking to identify vulnerabilities in their systems. This mutually beneficial arrangement allows you to leverage your skills, uncover security flaws, and earn money in the process. With …
Read More

Hacker vs Bug Bounty Hunters
Hacker vs Bug Bounty Hunters A Hacker is a criminal who breaks into systems illegally. A Bug Bounty Hunter is someone who is hired professionally by a company to penetrate and test vulnerabilities in a company’s software systems. However Sometimes real Hackers are hired as contractors to penetrate some systems, These are known as ethical hackers, Bug bounty hunters are …
Read More







