
The Top 20 OSINT Resources of the Year
Elevate Your Open Source Intelligence Gathering Because resources are needed in the Cyber Security Field we put together this comprehensive list of The Top 20 OSINT Resources of the Year Discover the Best OSINT Tools and Websites It’s crucial to mention, In the ever-evolving landscape of cybersecurity and digital investigations, staying informed and well-equipped is paramount. To sum it up, …
Read More

Top 20 Bug Bounty Platforms to Earn Money from
- Cyber Security
-
bug bounty, bug bounty platforms, bug bounty programs, cybersecurity, cybersecurity awareness, cybersecurity community, cybersecurity professionals, cybersecurity rewards, digital security, ethical hacking, hacker community, online security, penetration testing, responsible disclosure, responsible disclosure policy, security research, security researchers, security testing, security vulnerabilities, web security
- December 14, 2023
Top 20 Bug Bounty Platforms to Earn Money from Earn Big Money Hacking Fortune 500 companies! At the heart of ethical hacking and responsible disclosure, bug bounty programs connect security-minded individuals with organizations seeking to identify vulnerabilities in their systems. This mutually beneficial arrangement allows you to leverage your skills, uncover security flaws, and earn money in the process. With …
Read More

Who is the group called the hand?
- Cracking & Hacking
-
Honeypot traps., Illegal activities online, ISP monitoring, Online anonymity protection, ProtonVPN, Surveillance and privacy, The Five Eyes intelligence alliance, The Hand secret society, Underground organizations, VPN security
- September 26, 2022
Who is the group called the hand? “The Hand and the Five Eyes: An Overview of an Underground Secret Society” “Explore the enigmatic world of ‘The Hand,’ an underground secret society, often portrayed in movies and TV shows. Discover their connection to ‘The Five Eyes’ intelligence alliance and the importance of safeguarding your online anonymity. Learn which VPNs to trust …
Read More
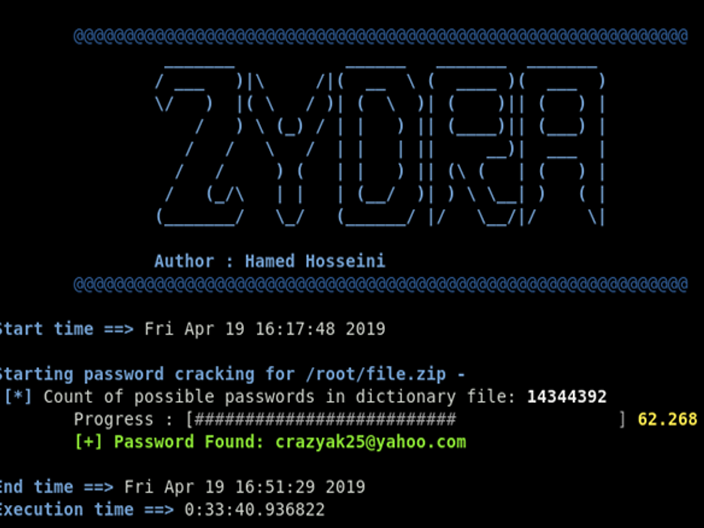
The Power of Zydra Cracking PDFS
- Cracking & Hacking
-
breaking PDF encryption, crack pdf, crack rar file, cracking encrypted PDF, decrypt PDF, hacking PDF files, password-protected PDF, PDF cracking software, PDF cracking techniques, PDF cracking tutorial, PDF decryption tool, PDF encryption, PDF hacking, PDF password attack, PDF password recovery, PDF security, remove PDF password, unlock PDF, winrar crack software, zydra, Zydra cracking tool, Zydra PDF crack, Zydra PDF cracking, Zydra PDF cracking guide.
- September 25, 2022
The Power of Zydra & Cracking PDFS “Unlock the potential of Zydra for PDF cracking. Explore the power of cracking encrypted PDFs effortlessly.” Some say, Eventually we find everything we are looking for on the internet, however, we never seem to be able to find the things we need at the time we need them. Zydra is no exception, It …
Read More

Hacker vs Bug Bounty Hunters
Hacker vs Bug Bounty Hunters A Hacker is a criminal who breaks into systems illegally. A Bug Bounty Hunter is someone who is hired professionally by a company to penetrate and test vulnerabilities in a company’s software systems. However Sometimes real Hackers are hired as contractors to penetrate some systems, These are known as ethical hackers, Bug bounty hunters are …
Read More

UI/UX Design Tips
UI/UX Design Tips 10 essential UI (user-interface) design tips Know your users. Define how people use your interface. Set expectations. Anticipate mistakes. … Give feedback—fast. … Think carefully about element placement and size. Don’t ignore standards. Make your interfaces easy to learn. UI/UX design examples How can I improve my UI UX design? Many examples of UI/UX sites are not …
Read More

Easy Photo Effects for Beginners
Easy Photo Effects for Beginners You will find that the easiest photo effect for Beginners would be a simple photo collage. Photo collages are a great exercise for beginners, because it allows you to practice putting composites together and cutting out images in photoshop without the guilt or risk of trying to make everything look 100% perfect. Collages are meant …
Read More






