How I Secured My WordPress Blog – A Real-World Cybersecurity Walkthrough
- Cyber Security
-
blog hardening, cybersecurity, ethical hacking, free security tools, kali linux, secure blog setup, website security, website vulnerability, Wordfence, WordPress
- July 31, 2025
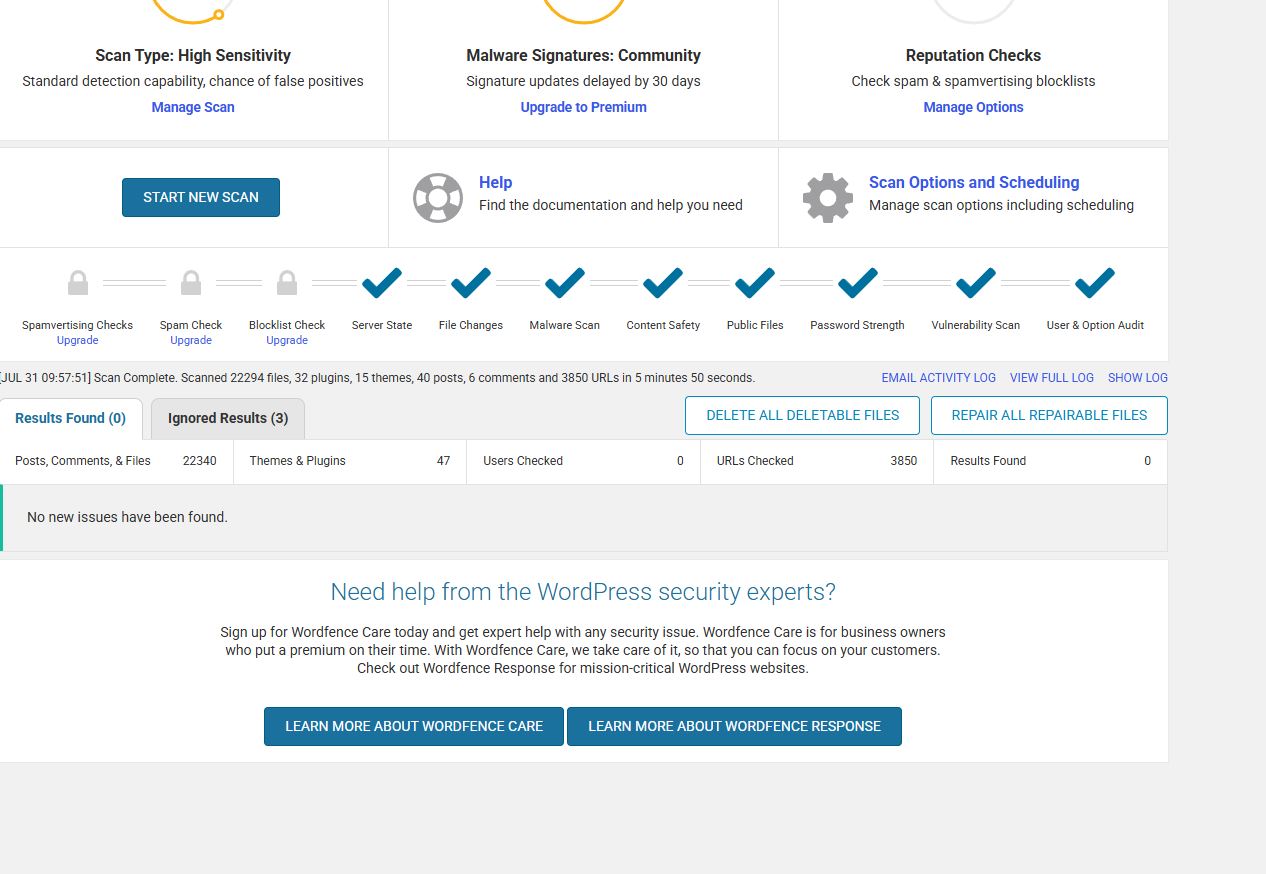
How I Secured My WordPress Blog – A Real-World Cybersecurity Walkthrough This post documents how I secured my WordPress blog using free tools, plugins, and configuration changes. The process simulates real-world website hardening and vulnerability management, which is useful for anyone studying cybersecurity, running a blog, or wanting to understand how attackers target insecure setups. Step 1: Scan Your Site …
Read More

How to Setup and Use Recon-ng
How to Setup and Use Recon-ng Setting up Recon-ng to install recon-ng you must have Python 3.6 or higher installed on your system, Please follow the instructions below to assist you in how to setup and use Recon-ng on your operating system. What is Recon-ng What is Recon-ng? Recon-ng is a web reconnaissance tool that automates information gathering to aid …
Read More

Kali Linux Basics: Cheat Sheet for Beginners
- Cracking & Hacking
-
cc cleaner, clear logs, clear tracks after hacking, cracking & Hacking, kali linux, kali linux cheat sheet, log cleaner, penetration testing, remove logs, shred clearing tracks, timestomp
- November 13, 2024
💻Kali Linux Basics: Cheat Sheet for Beginners November 05, 2024 Table of Contents 🧭 Navigation & Directory Management 📝 File Operations 🔍 Search for Files and Text 📦 Package Management with APT 🔒 Permissions and Ownership 📊 System Monitoring 🌐 Network Essentials 💾 File Compression and Archiving 🔧 Process Management ⏰ Scheduling with Cron 🔑 SSH & Remote Access 🧭 Navigation …
Read More


