How to hack a Website
- Cracking & Hacking
- brute force attack, cyber security blog, Default Credentials, How to Hack a Website, list of default passwords, LOGIN Bypassing Authentication, pentester blog, pentesting tutorials
- February 11, 2025
How to Hack a Website
- Inspect the Page Source: Right-click on the page and select “View Page Source” or press
Ctrl+U. Look for any comments or hidden elements that might contain hints or credentials.-
- Click on the browser’s menu icon (often represented by three dots or lines) in the top-right corner.
- Hover over “More tools” and select “Developer tools” or “View page source.”
- Using Keyboard Shortcuts:
-
Press Ctrl + U (Windows/Linux) or Cmd + Option + U (Mac) to open the page source directly
🤔What and where are we looking in the view page source?
Comments: Look for HTML comments enclosed within <!-- -->. Developers sometimes leave notes or hints that might be useful.
Hidden Inputs: Search for <input type="hidden"> fields. These can contain data not visible on the page but accessible through the source code.
JavaScript: Identify any <script> tags. JavaScript functions might include variables or functions that handle password validation or provide clues.
Meta Tags: Check for <meta> tags, especially those with name="description" or name="keywords". They might contain descriptive information about the page.
- Search for Keywords:
- Use the browser’s “Find” function (
Ctrl+ForCmd+F) to search for terms like “password,” “pass,” “key,” “hint,” or “protected.” This can quickly direct you to relevant sections.
- Use the browser’s “Find” function (
- Analyze URLs and Links:
- Look for URLs within
<a href="">tags or form actions. They might point to resources or scripts that handle authentication.
- Look for URLs within
- Review Inline Styles and Classes:
- Inspect elements with inline styles or specific classes that might indicate hidden or protected content.
✨Check for Default Credentials or use LOGIN Bypassing Authentication with Always-True Conditions✨
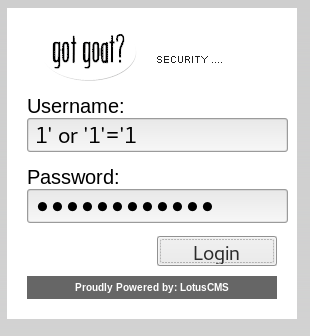
LOGIN Bypassing Authentication
For login on website
admin’OR’1’=’1
password123admin’–
PASSWORD123for password only fields
‘ OR ‘1’=’1
- Inspect elements with inline styles or specific classes that might indicate hidden or protected content.
- Check for Default Credentials: Some sites use default usernames and passwords. Common combinations include
admin/admin,admin/password, oruser/user. Attempt these to see if they grant access
.Research Common Default Credentials:
- Manufacturers often use standard usernames and passwords for initial access. Common combinations include:
- Username:
admin - Password:
admin,password, or1234
- Username:
- For a comprehensive list, refer to resources like the List of Default Passwords.
Kali Linux Tools and Methods
- Manufacturers often use standard usernames and passwords for initial access. Common combinations include:
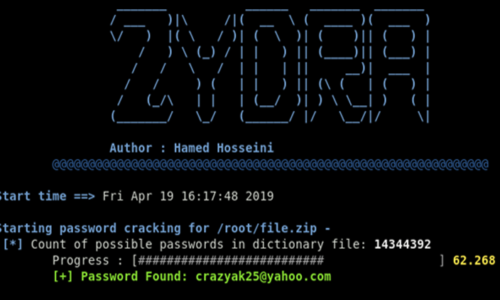
- Brute Force Attack: If allowed within the CTF rules, use tools like Hydra or Burp Suite to perform a brute force attack on the login form. This involves systematically trying a list of potential passwords until the correct one is found.
- Directory Enumeration: Use tools like DirBuster or Gobuster to discover hidden directories or files on the server. These might contain sensitive information or backup files that could help in bypassing authentication.
- Social Engineering: Sometimes, clues can be found in publicly available information. Research the organization for common password patterns or publicly shared documents that might contain useful information.
For more advanced methods
🙂 Follow us!
#WebsiteHacking #PenTesting #EthicalHacking #CyberSecurity #WebExploits
Leave Your Comment Here
You must be logged in to post a comment.